The Software Update Wizard lets you add 'update over the web' functionality to your applications with just a single line of code. You simply upload your revised software files, together with a simple script, to your web server. No server-side processing is needed, so this solution works with any server or ISP. The Software Update Wizard is a single, one-off, non-recurrent cost - there are no ongoing fees or additional costs.
The software solution can be used to free up space on your hard drive, erase junk or obsolete files, as well as detect and repair registry errors. On the other hand, you can rely on Baidu PC Faster to regularly scan your PC and make sure that none of your files are infected. On the other hand, you can rely on Baidu PC Faster to regularly scan your PC and make sure that none of your files are infected.
Dr.Web Security Space is a complete solution that will allow you to protect your computer against various external threats. Dr.Web Security Space brings you several security tools that work together to provide the best protection for your PC. Comprehensive anti-virus solution for PC Real time protection Best at curing active infections Installs in an infected system without its preliminary curing Fast multi-thread scanning Unique technologies blocking even unknown threats Full scan of archives at all nesting levels Best detection and neutralization of complex viruses Filters spam and other types of unsolicited messages without training the anti-spam Reliable on-the-fly scan of inbound and outbound homepage Efficient protection of children against exposure to objectionable content Protects against unauthorized access by a network; prevents data leaks; blocks suspicious connections on package and application layers New! Remote administration from other computers in the local network without installing the Dr.Web Control Center.
Advanced Task Manager is a program that focuses on keeping your computer secure and helping you find and disable spyware rapidly. Advanced Task Manager shows you exactly what is running on your computer, including the hidden processes. You can view the details of each process, including a security rating and security details such as whether a program connects to the Internet, watches what you type, is an Internet server, is hidden, is encrypted on disk, has invisible windows, etc. The security rating of a program indicates the likelihood of it being a virus, spyware, trojan, etc. If you discover a rogue program you can easily stop, quarantine or uninstall it so it doesn't run anymore. You can also manage your Windows startup programs with the included Startup Manager. Several other tools offer you detailed information about Internet connections, DLL files, CPU and memory use, Internet server programs running on your computer.
Get set to represent. Nitto 1320 Legends is a free multiplayer online drag racing game featuring the hottest cars and realistic performance tuning. Earn cash to collect your favorite cars, upgrade and tune your engine, then take it to the track. You can race head-to-head or in tournaments. Do you have what it takes to be the best? A list of some cars available to play: Integra GS-R, RSX Type-S, Integra Type-R, S2000, NSX , NSX Race Edition, Civic Si, RX-7, RX-7 Dragster, Bergenholtz Mazda 6, Mazdaspeed3, RX-8, GT, Mustang BOSS 429, Mustang GT, G35 Coupe, 350Z, tC, Supra, xB, Camaro SS, Camaro Z28, GTR, and Ford GT.
It’s always been our philosophy at AVG that everyone has the right to basic computer security at no charge. And our 80 million users think we’re doing a pretty good job. So if you’re planning to spend time online and you regularly exchange files with friends, check us out. * Surf, and search with confidence, while LinkScanner® keeps you safe from harmful sites * Get online and offline protection from viruses, spyware, and other nasties * Enjoy consistently high-speed PC performance with our new enhanced virus scanner * Automatic updates keep your protection current * Compatible with Windows XP, Vista, and Windows 7 AVG Anti-Virus Free Edition is an anti-virus protection tool available free of charge to home users. Rapid virus database updates are available for the lifetime of the product, thereby providing the high level of detection capability. The new 9.0 edition is faster, safer and easier to use. AVG Anti-Virus Free Edition gives you free rock solid protection for your basic security needs. The combined anti-virus/anti-spyware scanner in AVG Anti-Virus Free Edition runs up to 50% faster than earlier versions and doesn't get in your way. AVG Anti-Virus Free Edition also delivers new anti-phishing detection techniques, which can quickly and accurately determine whether or not a web page is hosting a phishing attack. Additionally, version 9.0 comes with basic anti-rootkit protection to ensure protection against sophisticated hidden threats. Features: · Surfing and searching the web and in your social networks LinkScanner Active Surf-Shield: · Ensures every web page you visit is safe – even before you go there. LinkScanner Search-Shield: · Applies safety ratings to your Google, MSN and Yahoo search results. Phishing Protection: · Checks to make sure web pages really are what they appear to be. · Emailing, Instant Messaging and downloading music and files E-mail Scanner: · Keeps you safe from dangerous attachments and links in your e-mail. · Whether you’re online or offline Anti-Virus: · Makes sure you can’t get or spread a virus, worm, or Trojan horse. Anti-Spyware: · Prevents unauthorized information access by spyware and adware. Basic Anti-Rootkit protection: · Ensures basic protection against sophisticated hidden threats. Update Manager: · Makes sure you’re always safe from the latest threats – automatically.
Easy Karaoke Player plays karaoke, records karaoke song to wav file. Easy Karaoke Player can play all kinds of multimedia files with a build-in powerful multimedia player. Easy Karaoke Player plays many audio formats such as MP3, MIDI, KAR, WAV, WMA, AC3, OGG, MPA, MP2, AU, AIF, SND, etc., and video formats VCD, MPEG, AVI, WMV, ASF, OGM, DIVX, DAT, SVCD etc. You can sing your favorite song and record it to high quality WAV file. You can download the trial version of Easy Karaoke Player freely.
Silverlight is a powerful development platform for creating engaging, interactive user experiences for Web, desktop, and mobile applications when online or offline. This latest version of Silverlight 4 delivers hundreds of features and controls that, when combined with the continued innovation in Microsoft’s world-class tools for designers and developers, Microsoft Visual Studio and Microsoft Expression Blend, present the leading edge in rapid, powerful application development. Silverlight 4 Information: This latest version of Silverlight delivers hundreds of features and controls that, when combined with the continued innovation in Microsoft’s world-class tools for designers and developers — Microsoft Visual Studio and Microsoft Expression Blend – present the leading edge in rapid, powerful application development. With printing support, rich reporting and charting, and integration with back-end systems and server products including Microsoft SharePoint, Silverlight is ready for business. Silverlight 4 delivers a full suite of powerful capabilities to business application developers, bringing the best-of-breed .NET platform to browser-based experiences. Silverlight provides an ideal platform for developing and deploying modern business applications for both customer facing and staff-facing applications. Business Application Development Silverlight 4 consolidates its position as the natural choice for building business applications on the Web: New Features for Application Developers * Comprehensive printing support enabling hardcopy reports and documents as well as a virtual print view, independent of screen content. * A full set of forms controls with over 60 customizable, styleable components. New controls include RichTextbox with hyperlinks, images and editing and Masked textbox for complex field validation. Enhanced controls include DataGrid with sortable/resizeable columns and copy/paste rows. * WCF RIA Services introduces enterprise class networking and data access for building n-tier applications including transactions, paging of data, WCF and HTTP enhancements. * Localization enhancements with Bi-Directional text, Right-to-Left support and complex scripts such as Arabic, Hebrew and 31 new languages including Vietnamese and Indic support. * The .NET Common Runtime (CLR) now enables the same compiled code to be run on the desktop and Silverlight without change. * Enhanced databinding support increases flexibility and productivity through data grouping/editing and string formatting within bindings. * Managed Extensibility Framework supports building large composite applications. * Exclusive tooling support for Silverlight, new in Visual Studio 2010. Including a full editable design surface, drag & drop data-binding, automatically bound controls, datasource selection, integration with Expression Blend styling resources, Silverlight project support and full IntelliSense. Developer tools * Fully editable design surface for drawing out controls and layouts. * Rich property grid and new editors for values * Drag and drop support for databinding and automatically creating bound controls such as listbox, datagrid. New datasources window and picker. * Easy to pick styles and resources to make a good looking application based on designer resources built in Expression Blend. * Built in project support for Silverlight applications * Editor with full intellisense for XAML and C# and VB languages.
This poker simulation offers the complete range of Texas Holdem Poker with realistic 3D graphics! An animated tutorial explains the poker rules. The environment and the rules are individually configurable and due to 3 levels of difficulty both professionals and rookies get their moneys worth. Additional to the single player mode and tournament mode with up to 160 players also multiplayer mode is available: you can either play over LAN or match up with others over the internet. Texas Holdem Poker "All-in": more is not possible!
CDBurnerXP is a free application to burn CDs and DVDs, including Blu-Ray and HD-DVDs. It also includes the feature to burn and create ISOs, as well as a multilanguage interface. Everyone, even companies, can use it for free. It does not include adware or similar malicious components. Key Features: * burn all kinds of discs * audio-CDs with or without gaps between tracks * burn and create ISO files * data verification after burning process * create bootable discs * multi-language interface * bin/nrg ? ISO converter, simple cover printing and much more! * Operating Systems: Windows 2000/XP/2003 Server/Vista/2008/Win7/Win8 (x86 / x64) Features: Create Data-CDs/DVDs · burn any Data on CD-R/CD-RW/DVD R/DVD-R/DVD RW/DVD-RW, including double layer mediums · burn mp3-CDs to store many audio files on one single disc · create bootable discs · verify written Data automatically after burning process · use either the internal browser to add your files or the intuitive Drop-Box to drag and drop files directly from any Windows Explorer window · save your compilations for creation of backups · burn on-the-fly and with buffer-underrun protections · import previous (ISO 9660) sessions and edit existing file structure on CD/DVD · quick- and full-erase disc · copy data discs (possible copy-protection is not bypassed) · retrieve recorder and disc information Create Audio-CDs · create Audio-CDs from mp3, wav, ogg and wma files · add single or multiple tracks from existing audio-CDs directly to your new compilation without ripping tracks before (add cda-files) · play audio-files with integrated audio player · gapless audio-CDs supported (disc-at-once-mode) · import M3U or WPL playlists ISO features · burn ISO files to CD · create your own ISO files · convert bin- and nrg-files to ISO · save CDs/DVDs as ISO file to disc Other features · simple cover printing feature for data- and audio-discs · supports most IDE, USB, Firewire and SCSI drives · integrated option to enable access to drive for restricted users · multi-language interface · online update
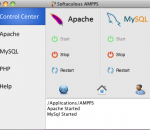
AMPPS is a stack of Apache, PHP, MySQL, Perl & Python. AMPPS enables you to focus more on using applications rather than maintaining them. With AMPPS you can create a website by installing any of the 300+ Apps, customizing it, and then simply publishing it on the internet via a wide choice of hosting service providers.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.