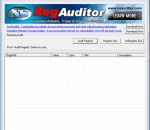
Registry Auditor gives you a quick look at the Adware, malware and spyware installed on your computer including parasites and trojans. Registry Auditor tells you by colored icons ( green icon - safe, yellow icon - unknown, red icon - harmful ) whether specific Objects are known to be safe or harmful, also the program searches the registry for entries including filenames that aren't present on and allows you to delete unwanted registry entries.
avast! Home is a free antivirus, anti-spyware and anti-rootkit solution for non-commercial home use. It scans for all forms of malware. avast! antivirus has obtained VB100% award, AV-Comparatives, ICSA Labs and many more. avast! scans: On Demand - with Skinnable Simple Interface, during Boot Time and On Access. It protects E-mail, HTTP, NNTP, ICQ, mIRC, Kazaa etc. True low bandwidth incremental updates.
Acronis Backup and Recovery 10 Online - a fast, secure and cost-efficient offsite data protection service from the leader in local and online disaster recovery. This subscription service, when used in conjunction with Acronis Backup & Recovery 10, offers the benefits of a dedicated remote datacenter providing backup & recovery redundancy without the high price tag.
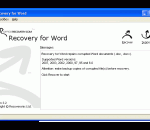
Recovery for Word fixes corrupted Microsoft Word document files (.DOC). With Microsoft Word 2010 support, a great new user interface and numerous improvements to the recovery engine, the latest Recovery for Word is a most advanced document data recovery program available. Supports all modern file versions, including Word 2010/2003/XP/2000/97/95/6.0 documents. Recovers text and formatting. Recovers password-protected files (if password is known).
RollBack Rx is a robust system restore utility that enables PC users to easily restore a PC to a time before certain events occurred. RollBack Rx makes it easy for users of all skill levels to quickly and easily repair PC issues - saving time, money and PC trouble. With RollBack Rx you can... Reverse any system crash (even if Windows can't startup) Backout of any failed software installations, botched OS update and more...
Iperius Backup is a lightweight, flexible and reliable backup software: Disk imaging, backup to NAS/RDX, file synchronization and zip compression, backup to Tape DAT/LTO, AES encryption, backup to FTP and to Google Drive, Dropbox and SkyDrive (cloud backup), Oracle backup, SQL Server, MySQL MariaDB, PostgreSQL, database backup. It can make backups on many devices and send e-mail notifications. Freeware edition. Windows 8 / Server 2012.
Lynx VirusScan is a small, compact and easy to use application that will enable you to scan and remove malware components from your computer.
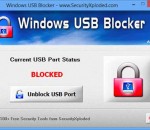
Free Windows USB Blocker or Unblocker Tool
Stinger is a stand-alone utility used to detect and remove specific viruses. It is not a substitute for full anti-virus protection, but rather a tool to assist administrators and users when dealing with an infected system. Stinger utilizes next generation scan engine technology, including process scanning, digitally signed DAT files, and scan performance optimizations.
Delphish - Technology by SaferSurf --> Protects your computer against phishing, malware and spam. SaferSurf operates the fetching of e-mails and inspects all data transferred between your computer and your mailbox. phishing e-mails, spam and e-mails containing malware are blocked before they reach your computer. The filtering is done centrally on the safersurf server. Mailware and unwanted e-mails do never get in touch with your PC.
McAfee Labs Stinger is a stand-alone utility used to detect and remove specific viruses. It is not a substitute for full anti-virus protection, but rather a tool to assist administrators and users when dealing with an infected system. Stinger utilizes next generation scan engine technology, including process scanning, digitally signed DAT files, and scan performance optimizations.
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Kaspersky anti-virus protects you from the Phishing and Malware sites that you wouldn't otherwise know were attempting to steal from you. At the same time, the Kaspersky Security Network allows your computer to report when it discovers a threat that hasn't been seen before. All 250 million Kaspersky users benefit from our combined knowledge! Kaspersky features include: Protects from viruses, Trojans, worms, spyware, adware Scans files, email, and internet traffic Protects Instant Messengers Protects From Unknown Threats Analyzes and closes Internet Explorer vulnerabilities Disables links to malware sites / phishing sites Global Threat Monitoring (Kaspersky Security Network) Blocks all types of keyloggers Automatic Database Updates Free Technical Support Note: This is a 30-day commercial trial.