Unformat 3.0 is a software utility for those who have accidentally deleted or formatted a hard disk partition or any other kind of digital storage media. The latest edition sports a number of scanning improvements as well as over thirty new file signatures to search for recoverable files of less common formats. For those seeking to unformat hard drive partitions or data on any other digital media, this software provides the features you need.
BitDefender Free Edition is your chance to use one of the world's most effective antivirus engines for free! BitDefender Free Edition uses the same ICSA Labs certified scanning engines found in other BitDefender products, allowing you to enjoy basic virus protection for no cost at all. BitDefender Free Edition is an on-demand virus scanner, which is best used in a system recovery or forensics role. Features and benefits include: Virus scanning and removal On demand scanning - Powerful scan engines ensure detection and removal of all viruses in the wild every time you need it. Scheduled scanning - The Scheduler lets you plan ahead, and schedule full system/drive scans in the off hours, when you won't be using your computer. Immediate scanning - With just a right click you can check your files and folders. Skinable interface - You can express yourself, designing new interfaces, or you can use those drawn by others. Quarantine - By isolating the infected files in quarantine, the risk of getting infected diminishes. You also have the possibility to send these files for further analysis to BitDefender Labs. Reports - When launching a scan you may choose to create a report file where you can see statistics about the scan process.
URANIUM BACKUP Uranium is a complete and reliable backup software for Windows available in both free and commercial editions. Discover the advantages, try Uranium.
Casper makes maintaining a backup replacement disk for your PC easy by creating a complete, immediately-bootable copy of your PC's hard disk, including the operating system, applications, settings, and all of your data. If your PC's hard disk fails or becomes corrupted, boot your computer directly from your backup hard disk and you're up and running again in seconds. Automate the backup to be performed at any time -- even while you use your PC.
Beyond Compare 3 is the ideal tool for comparing files and folders on your Windows system. Visualize changes in your code and carefully reconcile them. Compare Files, Folders Beyond Compare allows you to quickly and easily compare your files and folders. By using simple, powerful commands you can focus on the differences you're interested in and ignore those you're not. You can then merge the changes, synchronize your files, and generate reports for your records. Specialized Viewers Beyond Compare includes built-in comparison viewers for a variety of data types. Compare .csv data or HTML tables in a Data Compare session, or images in a Picture Compare session. 3-way Merge Beyond Compare's new merge view allows you to combine changes from two versions of a file into a single output. Its intelligent approach allows you to quickly accept most changes while carefully examining conflicts. Synchronize Folders Beyond Compare's intuitive Folder Sync interface lets you reconcile differences in your data automatically.
Titanium Antivirus Plus: Essential Protection Trend Micro Titanium™ Antivirus Plus provides easy-to-use security for the tasks you do every day—email, socialise, and surf the web, hassle free. It features: * Antivirus and Antispyware * Antispam * Social networking security * Facebook Privacy Scanner * Windows 8 Secure Browser Titanium is protection made easy. Trend Micro Titanium Antivirus Plus makes security effortless by providing you with a friendly interface that’s a snap to install. It features set-and-forget protection that won’t pester you with annoying alerts and pop-ups. Key Benefits: * Blocks viruses, malware, and dangerous links shared through email and IM * Identifies safe and malicious search result links in Chrome, Internet Explorer, and Firefox * Identifies safe and malicious links in popular social networking sites like Facebook, Twitter, Google+, LinkedIn, and Pinterest * Features a friendly interface that’s a snap to install and use * Provides you with simple screens and clear, easy-to-understand reports Features: Strong antivirus protection made easy From the Titanium main console screen, you can easily run antivirus scans, get up-to-the-minute status reports on your computer's security, and use short cuts to features like the Facebook Privacy Scanner. You can also view the status of your protection, including details about the software, online help, and account information. Detailed security reports Easy-to-read reports give you the details on current computer threats. You can see detailed logs with just one click. Social networking protection Titanium’s social networking security automatically scans your Facebook wall or Twitter feed and shows you safe links by highlighting them in green. Potentially malicious ones are highlighted in red. The colour-coding relies on Trend Micro's cloud-based Smart Protection Network™ infrastructure that continuously analyses threat behavior. When Titanium identifies a bad link, it will even let you easily and quickly warn your friend. Titanium can protect you online and help keep your friends safe too. Facebook Privacy Scanner Titanium’s new Facebook Privacy Scanner provides you with another layer of protection. With a single click, it lets you easily monitor your Facebook page settings and control who can contact you and access your personal information. Titanium will identify which settings may lead to privacy concerns. This feature lets you control which apps can access your bio, who can tag you, see your photos, and more. Web threat protection Titanium pre-sets web threat protection to block malicious links and downloads in emails, instant messages, or websites. This recommended level of security protects you from online phishing scams that try to steal credit card or other personal financial information. You will be warned of unsafe web pages and blocked from accessing them. Personalise your Titanium Customise your Titanium software user interface with a favourite photograph or image. Simply upload your chosen picture to personalise your Titanium experience.
HijackThis inspects your computers browser and operating system settings to generate a log file of the current state of your computer. Using HijackThis you can selectively remove unwanted settings and files from your computer. Because the settings identified in a HijackThis log file can belong to both legitimate software and unwanted malware, it is important to use extreme caution when choosing to removing anything using HijackThis. HijackThis also comes with a process manager, HOSTS file editor, and alternate data stream scanner.
GiliSoft USB Stick Encryption is especially designed to create password protected USB memory sticks. It creates protected areas on the disk that is needed to enter password to see contents. Data on the protected areas are encypted by 256-bit AES on-the-fly encryption. Protected USB stick is fully autonomous and does not need any special software installed on computer.
RootkitRevealer is an advanced rootkit detection utility. It runs on Windows NT 4 and higher and its output lists Registry and file system API discrepancies that may indicate the presence of a user-mode or kernel-mode rootkit. RootkitRevealer successfully detects many persistent rootkits including AFX, Vanquish and HackerDefender (note: RootkitRevealer is not intended to detect rootkits like Fu that don't attempt to hide their files or registry keys). Since persistent rootkits work by changing API results so that a system view using APIs differs from the actual view in storage, RootkitRevealer compares the results of a system scan at the highest level with that at the lowest level. The highest level is the Windows API and the lowest level is the raw contents of a file system volume or Registry hive (a hive file is the Registry's on-disk storage format). Thus, rootkits, whether user mode or kernel mode, that manipulate the Windows API or native API to remove their presence from a directory listing, for example, will be seen by RootkitRevealer as a discrepancy between the information returned by the Windows API and that seen in the raw scan of a FAT or NTFS volume's file system structures.
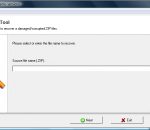
ZIP Viewer Tool is a specialized tool for viewing damaged archive files of the ZIP format and recovering data from them. A professional solution created for everyone, the program opens corrupted ZIP archives and restores their contents with a few mouse clicks thanks to its advanced file analysis engine that uses a combination of several algorithms to achieve the best recovery efficiency.
Deep Freeze has changed the way IT Professionals approach end-point security; its non-restrictive concept offers the most robust workstation protection available. The need for IT professionals to perform rebuilds, re-image, or troubleshoot computers is eliminated with Deep Freeze's reboot-to-restore technology. The result is a dramatic reduction in support and IT expenditures and a substantial increase in computer uptime.
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Kaspersky anti-virus protects you from the Phishing and Malware sites that you wouldn't otherwise know were attempting to steal from you. At the same time, the Kaspersky Security Network allows your computer to report when it discovers a threat that hasn't been seen before. All 250 million Kaspersky users benefit from our combined knowledge! Kaspersky features include: Protects from viruses, Trojans, worms, spyware, adware Scans files, email, and internet traffic Protects Instant Messengers Protects From Unknown Threats Analyzes and closes Internet Explorer vulnerabilities Disables links to malware sites / phishing sites Global Threat Monitoring (Kaspersky Security Network) Blocks all types of keyloggers Automatic Database Updates Free Technical Support Note: This is a 30-day commercial trial.