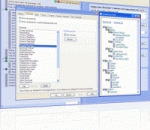
With SiteXpert you can create a professional navigation scheme (such as a DHTML drop down menu or site map tree) within a few minutes. No JavaScript knowledge is required. All you need to do is pick a base URL and let the program crawl through your website. SiteXpert can also scan your directory / file structure to automatically build a navigation system for your web site. Xtreeme SiteXpert Standard Edition is an application which can created 10 different navigation system types (static and dynamic site map tree, DHTML / Javascript drop down menu, portal interface, site index, Java applet site map tree, mega folder, hierarchical diagram and more..). Xtreeme SiteXpert comes with over 90 beautiful predefined graphical schemes. Menus and site maps can be easily inserted into existing web pages using includes (e.g. ASP / PHP / JSP / SSI / FrontPage / ColdFusion). Frames are supported in all types of navigation systems. JavaScript code generated by SiteXpert is highly compressed, depending on the features you choose and is compatible with all major browsers (Internet Explorer 4+, Netscape 4+, Opera 6+, Mozilla) and systems (Windows, Mac, Unix). SiteXpert can also validate your links and upload generated code to an FTP server. Here are some key features of "Xtreeme SiteXpert Standard Edition": · Highly optimized code compatible with every major browser · Lots of different navigation styles · You can fine-tune the menu appearance to the very detail · Automatic web site spidering with link validation · Creation of Google Sitemaps and ROR Sitemaps · Free DHTML Menu Studio included
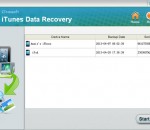
Data loss is always a big headache for people nowadays. No matter a computer user or Apple iOS device owner is possibly to suffer from such problem caused by many reasons. Once you are an iDevice user and rightly vexed about how to get your lost photos, text messages or other crucial stuff back to your iPhone, iPad or iPod, then why don't you let the iTunes Data Recovery do you a favor? From the coming up describes, you will well know this pr ...
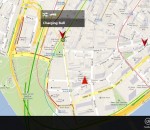
You can get directions from/to your location or between two coordinates/addresses. Different travel modes like 'Driving', 'Cycling', 'Walking' or 'Public transit' are supported. When a route is built, you can browse the route steps or select an alternate route.
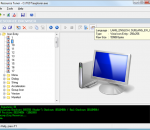
Resource Tuner can change the look of the icons, cursors, dialogs, buttons, sounds, animations and other elements of the Windows user interface by editing and replacing resources in the executable files (EXE, DLL, ActiveX controls and more). Quick and easy access to all the resources which are normally inaccessible really allows you completely customize any program you own.
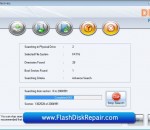
Flash disk repair software provides you safe and reliable way to easily restore all crucial data files from your formatted, logically crashed and inaccessible Fat media storage devices. Highly specialized file software is specially designed to easily handle all data loss problems for any FAT partitioned external HDD. Software provides you speedy and mighty way to unformat all accidently formatted important documents from inaccessible Fat drives
AIMP is more than an audio player: it supports numerous audio formats (including OGG, MP3, WMA, WAV, OGG etc), it includes an audio converter, an audio ripper, an audio recorder, a tag editor and lots of other features. You can also download additional plugins and skins from the official website. Mediaplayer - qualitative and pure playing multimedia of files, including mp3; good facilitys, the small size and minimal use of system resources. Note: Free for non-commercial use. Here are some key features of "AIMP": · Crystal-clear sound, technology of reproduction essentially differs from Winamp and WMP; · Sensitive equalizer; · A maximum of functionality from a minimum of resources; · The minimal consumption of system resources; · Multilingual support; · Support of set of formats of audio · Adjustment of global and local hot keys (patterns from WinAmp and WMP); · Flexible options of the program and various covers will allow you to make A.I.M.P. completely individual; · Support of plug-ins with which help it is possible to expand opportunities of the program; · The audioconverter codes music from the most different formats in wma, mp3, wav, ogg; · audioGrab allows to overtake AudioCD in Mp3, OGG, WAV or WM; · The sound recording will allow you to write down a sound from any audio of the device in system; · The built - in editor of tags, support WMA, MP3, OGG; · An opportunity of record AudioCD, MP3-disks and disks with given
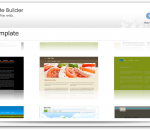
Pika Website Builder was developed as a simple and user-friendly web design software that allows you to create HTML websites. Pika Website Builder is an easy-to-use, fast and intuitive instrument that's built to fit all your development needs. Now, you can built amazing web pages in no time at all. Simple - makes it easy for anyone to use. Kick Start - choose from many of templates to get you going. Better. Faster. Easier. - Pika takes full advantage of SEO technology, ensuring search engine friendly sites. Compatibility - Websites created with Pika render effortlessly on Firefox, Chrome and Internet Explorer. Publishing - When you're done building your ideal site, seamlessly publish it to the web with the click of a button.
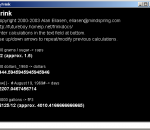
Frink is a practical calculating tool and programming language designed to help us all to better understand the world around us, to help us get calculations right without getting bogged down in the mechanics, and to make a tool that's really useful in the real world.
Mary Jane has been captured by Venom! Help Spider-Man reach her in time by swinging across the building tops before time runs out.
Try to keep the useful cards to yourself and avoid giving your opponent the upper hand! In this 2-player game, a deck of standard playing cards will be used. At the start of each round, the dealer will deal 6 cards to each player, and each player needs to discard 2 cards to the crib. A card from the remaining stock will then be dealt and displayed at the bottom right corner of the screen, and this card is the "starter". If the starter is a J, the dealer will be awarded 2 points. Cards in the crib and the starter will be reserved for later use. When the round begins, the player who is not the dealer can start by playing a card from his hand. Then the dealer can also play a card from his hand and the round continues. Each card played carries a certain amount of points, A has 1 point, 2 has 2 points, and so on, while each J, Q and K carries 10 points. The current count of points will be displayed on the left of the screen. The total point from the cards played must not exceed 31. If a player cannot play any cards, he needs to say "go" and the other player can play cards from his hand until he cannot do so. If the total point is exactly 31, the player who played the last card will get 2 points, otherwise he will receive 1 point. The count is then reset to 0 and the player who did not played the last card can start to play a card. Then the round continues until both players have run out of cards. During the round, you can also score points according to the following ways: 1) when the total point is exactly 15, the player who played the card will receive 2 points; 2) when at least 3 newly played cards form a run of consecutive ranks, the player can receive points equal to the length of the run, for example, the player can get 3 points for completing a run of three; and 3) when 2, 3 or 4 newly played cards are of the same rank, the player can receive 2, 6 and 12 points respectively. When both players have run out of cards, an additional scoring phase begins. For the
3D horror game. Collect 8 photos and escape from a prison while avoiding the Slenderman. Staring at the Slender Man will drain your sanity - losing your sanity will have negative effects and will likely get you killed. Sprinting will decrease your maximum stamina, so sprint only when required.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.