FileRescue for NTFS is an easy-to-use, yet powerful software utility, designed to restore accidentally deleted files and folders. It allows you to recover files that have been deleted from the Recycle Bin, as well as those deleted after avoiding the Recycle Bin (Shift-Delete). It will also recover files deleted by virus attacks and software faults. 100% FREE to try.
The Complete Set of Blocker Tools from SecurityXploded
BKF file recovery program repairs inaccessible BKF files of a system. It recovers data from corrupt Backup files that are created using NTbackup.exe or backup tool of Veritas Software. RecoveryFix for BKF is capable of recovering large data such as disk volumes from corrupt BKF files. It supports BKF files created on MS Windows, Novell and Macintosh OS platforms.
Lenovo Drivers Download Utility is the all in one solution in driver update software. The software is professional driver software which is capable of updating your Lenovo computer drivers and other Lenovo products. Lenovo Drivers Download Utility will update your Lenovo desktop drivers, Lenovo laptop drivers and different kinds of Lenovo printers. After the initial scan, Lenovo Drivers Download Utility matches your device with the latest Driver.
PC Agent monitors and records the activities of all users on a computer unnoticed. The monitoring captures not only the most common activities like keystrokes, visited websites and screenshots, but also Internet activities such as sent and received emails and many more. PC Agent is specially designed to send the records in several different ways.
Use Memory Card File Recovery Tools which is available at website www.filesrecovery.in to restore misplaced pictures, snapshots, video clips erased due to logical corruption, virus or worm infection, batter failure, human error, accidental data deletion, frequent formatting etc.
Advance keylogger utility is safe and secure utility that restricts illegal users to access/modify software settings using password authentication. Spy computer software records sound clips, audio/video files, pictures, documents explored by external user in your absence. Keyboard key recording utility is complete solution for parents, investigation agencies, educational institutions, corporate sectors etc to keep track on computer usage.
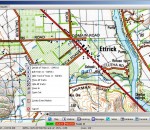
The user can add new map locations by entering the coordinates from the keyboard or by using the data from the GPS device. The Event Log system allows the user to view the important events and to add log entries.
UltraGram is a visual parser generator for professional software development. Application provides extended functionality for creating grammar of a parser, interpreter or compiler, testing it and generating parser source code in a preferred programming language.
Read only Ntfs Partition Data Restore software provides an inbuilt execution wizard facility to restore business file without any correction. Portable file recovery tool scans entire damaged hard disk drives partition to restore document save in any graphical extension like .txt, mkv, gif, jpg, jpeg, html, xml, mov, doc etc by taking less turnaround time and cost. Secure data undelete tool restore encrypted and compressed zip file within seconds.
Miraplacid Publisher converts any printable documents to images. Miraplacid Publisher supports following output formats: PDF, JPEG, TIFF, BMP, PNG, TGA, GIF and Web Presentation. Scale the image as you need, adgust colors and gamma, set output format and compression ratio, get rid of unused white borders. Save to file, upload to FTP or HTTP server, email or print to a real printer. Multi-page images suppor. Free SDK.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.