PeaZip is a free ZIP files utility and free RAR extractor, features encryption, secure deletion and file split. Create 7Z, BZip2, GZip, PAQ, PEA, QUAD/BALZ, split .001, sfx, TAR, WIM, XZ, ZIP files. Open and extract RAR, ARJ, CAB, DMG, ISO, JAR, LHA, MSI, UDF, ZIPX files and more (150+ types). Browse archives, multiple inclusion/exclusion filters, save archive layout, save and schedule task definition as script, work on multiple archives at once.
Download and archive entire websites such as forums, galleries, online books and articles. Copy and store websites on portable media such USB and CD. Download and convert websites from localhost, intranet, internet etc. Convert dynamic database driven websites into static. All links in the website can be converted to relative. Upload the downloaded website to mirrors and servers. Present websites to clients in offices with no internet access. Save webserver resources by not using server side code. Get everything from small to giant websites with many thousands of pages. Quickly download websites using multiple connections. Use include and exclude filters to control which files to crawl and list. Follow all kinds of references including redirects, frames, javascripts and images. Website downloader can even perform website login and handle cookies. Automate download of websites at times convenient to you, e.g. during the night.
Your every wish is fulfilled today! Space, which we know from astrology, the sun and the moon... It is so far away and so close to us... Stunning wallpaper that you will remember for the rest of your life. Astrology, which never turn away from you. It's Cosmogram!
AceText extends the Windows clipboard, enabling you to copy and paste like never before. Take notes, jot down ideas and keep important information at your fingertips. Use templates to quickly communicate via email or instant messaging. Never again type in the same message twice. Store and move around blocks of text to easily edit complex documents. Drag and drop text from web sites and compile research. Instantly find previously saved snippets.
Automatically have form submission data added to your MYSQL database with protection against form hijacking, email injection and email harvesting. On form submission a new record is added to the MYSQL database table and MYSQL database table fields that have the same name as form fields will include the input values from the form field. You can also include a range of User and Cookie Variables for automatic import into the MYSQL database.
American Billiard free - is a pool billiards simulator. Pool, also more formally known as pocket billiards or pool billiards, is the family of cue sports and games played on a pool table having six receptacles called pockets along the rails, into which balls are deposited as the main goal of play. Popular versions include eight-ball and nine-ball. This game can be played either against a computer or human opponents (on the same PC) on several playing tables. Training mode and trick shots available now. Exersices for beginners and advanced players. 8-Ball, 9-Ball, 3-Ball and Snooker games with additional rules hints. Lot of ball sets, animated 3d players. The program comes with a powerful anti-aliasing algorithm for the cue and balls, which minimizes video card resources required, freeing them to be used by other parts of the program. Features: . 3D Pool with additional arcade tables . Hints (3 types), Undo - Redo, Next Ball and balls highlights . 1 Player, 2 Player and Training modes . 8-Ball, 9-Ball, 14+1, 3-Ball, Snooker . AI skill levels: Easy, Medium, Professional . Program Balls render to correct geometry mistakes and full antialiasing. . Different Rooms . Sondtrack
Aplus DVD Ripper is design for backup your favorite DVD movie to your computer by converting DVD to AVI, DivX, XviD, VCD, SVCD, MPEG1, MPEG2, Apple iPod MP4 files, Apple iPhone MP4 files, Apple TV MP4 files , Youtube's Video, flv video , Sony PSP MP4 files, Cell phone 3GP files, Zune files, Pocket PC files , PDA files, Xvid files etc, before you rip, you can choose subtitle,audio track,frame rate and audio quality if needed. and its flexibility Output setting let you customize your generated Movie size. Aplus DVD Ripper use latest DVD rip technology support convert any DVD disc, Compatibility in NTSC and PAL format DVD movies. and any copyright protected DVD movies. Key Features: 1).Convert DVD to MPEG1,MPEG2,MPEG4. 2).Convert DVD to VCD,SVCD. 3).Convert DVD to AVI,DivX,XviD. 4).Convert DVD to Apple iPod MP4 files. 5).Convert DVD to Apple iPhone MP4 files. 6).Convert DVD to Apple TV MP4 files. 7).Convert DVD to youtube's Video files. 8).Convert DVD to flv Video files. 9).Convert DVD to Zune Video files. 10).Convert DVD to Sony PSP MP4 files. 11).Convert DVD to Cell phone 3GP files. 12).Convert DVD to Pocket PC files. 13).Convert DVD to PDA files. 14).Support Ripping DVD by custom file size. 15).Support choose subtitle and Audio track to rip. 16).Support Setting Beginning and Ending point to rip. 17).Normally, the conversion speed is 3 times of the playback speed. 18).Support Automatically Shut down your computer after long time conversion. 19).Best quality: the support for the latest industry standards ensures the videos you create with best picture and audio quality.. System Requirements: OS Supported: Windows 98/ME/NT4/2000/XP/2003 Hardware Requirements: Intel Pentium II 350MHz or above 64 MB RAM or above DVD-ROM
Time to showcase your matching skills, mahjongg lovers! Your goal in this game is to remove all tiles by pairing them up. Before the game starts, you can choose to play with the classic mahjongg set or a simple combination of numbers and letters. Simply click to select the set you like to begin. Then the chosen set will be piled up. When you find a matching piece of a tile, you can click the two pieces so that they can be removed. Note that only the topmost piece on a pile which is not blocked from the left or the right can be taken. The tiles that can be removed will be highlighted in red when you click them. A timer at the top left corner will count the time you have spent, while your score will be counting down from 10000 according to the time. If you are not able to make any moves, you may click the Restart button on the left to start over. You may also click the Hint button to receive a hint, but note that each time you do so 600 points will be deducted. Play the interesting mahjongg solitaire and feel the oriental ambiance!
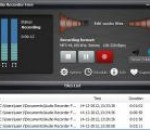
Audio Recorder Free is useful real-time audio recording software that lets you record any sound from your computer such as microphone, line-in audio, streaming audio from online radio station, audio played by media players, DVD audio directly into high quality MP3, WMA, OGG or WAV files. Furthermore, you can edit the recordings with the built-in audio editor and then share it - burn CDs, upload to the web, or export as MP3 for listening on your favorite portable players. Audio Recorder Free brings you a new way to enjoy music! As a free sound recorder program, Audio Recorder Free does exactly as it sounds - record any sounds from your sound card. It records streaming audio from any web site for offline enjoyment; records cassette recordings you cherish to save them on a computer and then burn a CD backup or entertainment; records old vinyl recordings, clean them up, and make them fit for digital consumption; record VoIP (Voice over IP) calls or internet-telephony conversations; record DRM-protected music to create private and unprotected copies that can be suitable with your iPod, iPhone or any other portable players. The inbuilt time triggered recording has the ability to schedule a recording automatically on the Once, Daily and Weekly you choose and releases your much time to deal with your job or other obligations. It enables saving the recorded audio files in different popular formats such as MP3, WAV, WMA and OGG while specifying the sound quality for the best performance. The AGC helps increase and equal overall sound volume level of the recordings and VAS helps skip silence passages or stop the recording after a certain amount of silence. To make your recording work easy, Audio Recorder Free keeps the recorder window above the other windows; allows you to define your own hotkeys to control the recording tasks; automatically names the recordings by date & time, skips silence or stops recording if silence is detected from the signal, etc.
NestLib is a high speed true shape automatic nesting software for optimizing material utilization while fitting two-dimensional shapes on a larger sheet. Various advanced features like Common line nesting, Multiple Torch nesting, Cluster nesting, Grid nesting, Automatic sheet size selection, Optimal nesting makes NestLib the best solution in the industry. NestLib is available in DLL form and also as online nesting service.
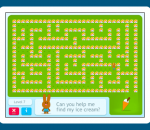
Maze Book 3 is another set of computer generated mazes for kids. In this set, kids guide animal characters through mazes in Animal Town to find friends, neighbors, teachers, toys, and lots of other characters and objects. With three levels of difficulty, kids can find the level of challenge that is right for them. Unlike paper and pencil mazes, Maze Book 3 is interactive -- kids guide characters through a variety of bright, colorful mazes finding objects. Not only will kids have lots of fun with these mazes, but they will gain hand-eye coordination, visual tracking, and problem solving skills. Download a free trial version of Animal Town Maze Book that you can use indefinitely! Published by Dataware.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.