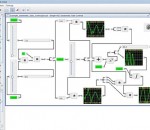
JMCAD is an program for the modeling and simulation of complex dynamic systems. This includes the ability to construct and simulate block diagrams. The visual block diagram interface offers a simple method for constructing, modifying and maintaining complex system models.
PCL Reader views & converts PCL to PDF, PDF/A, XPS,TIF, BMP, PNG, JPG, PCX and Text. Once viewed, a PCL or Text file can be printed to any Windows printer driver. This is useful when you have a non-LaserJet PCL printer and need to print an invoice, loan, or other type of PCL document from legacy applications that require PCL4/5/5e LaserJet printers. ASCII text can also be extracted from the PCL for data migration and archiving.
Unpack Monitor is a solution to the annoying issue on unraring files.It monitors folders you’ve selected, and unpack to a selected unpack folder. So no more unpacking when you have the time, just start the program, and when you return, all the files are already unpacked, and ready for use.
.Net Active Directory Lite is a free package of two Visual Studio solutions (.sln) that includes all the source code to calling multiple Active Directory function and a complete sample application that demonstrates the functionality of the wrapper. Both solutions are written in C# and are combatible with both .Net Framework 1.1, 2.0 and 3.0.
When TCP Spy's Start button is pressed, it will capture and display all socket calls of the next application that starts and makes a socket call. It will also capture and display the data that is sent and received on the application's sockets. The application can be of any type. TCP Spy displays its output in a scrollable text box. This data may additionally be sent to a file as text or HTML. By default, only 32KB of data is kept in the scrollable text box. Higher data limits may be selected, including unlimited. Based upon each socket's first transferred message, TCP Spy will determine if the protocol being communicated over the socket is text based. If so, TCP Spy will test each following message for text. If a message contains only text, TCP Spy will display it as such. Else, TCP Spy will show the message in hexadecimal and ASCII. If the protocol is HTTP, the HTTP headers will be displayed as text. Without a license, TCP Spy does not provide the option of sending data to a file, and only keeps 32KB of data in the scrollable text box. When you register TCP Spy, you will be sent a code that enables the additional features.
WinPatrol takes snapshot of your critical system resources and alerts you to any changes that may occur without your knowledge. WinPatrol was the pioneer in using a heuristic behavioral approach to detecting attacks and violations of your computing environment. It continues to be one of the most powerful system monitors while staying a single small programs.
The most important part of designing a new site is the navigation or menu system, but this can be tricky, time consuming and often frustrating. You need something that will fit into your design and most importantly, allow your readers to navigate with ease. jQuery Drop Down Menu is a multi level, CSS list based menu powered using jQuery that makes website navigation a smooth affair.
ASP Component / COM object to create and edit animated GIFs. Read GIFs from disk, data stream or remote URL, save to disk or export to the browser. Draw text and simple shapes. Resize, rotate, crop, flip. Edit colour tables and frame properties. Optimisation method to reduce file size. Free trial available with full instructions. 32 bit or 64 bit.
Goldfish is the easy to use solution for creating gorgeous, individual websites in little time. In the last few years Goldfish developed from a small tool to a widespread website creator with a growing user base. Creating websites with Goldfish is not as static as if you use a template-based application. These applications are often compared to Goldfish, but they only allow to fill precast website templates.
Most everyone has files or folders on their computer that they do not want to share with others. Free Hide Folder is a free computer security software to hide your private folders. Others will not know where your personal files exist and they will not be able to accidentally view them. You can hide folders simply with a few mouse clicks. Free Hide Folder is protected by a password that you can change or remove at any time.
haXe was designed to be a high-level object-oriented programming language with the intention of helping programers develop Websites and Web applications. haXe has been designed to be easily portable across several platforms.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.